// VULNERABILITIES_ARCHIVES
Getting React2Shell Vulns Under 1 Minute
Practical script for React2Shell vulnerability, covering CVE-2025-55182 and CVE-2025-66478 fastest interaction. For an overview, I already c
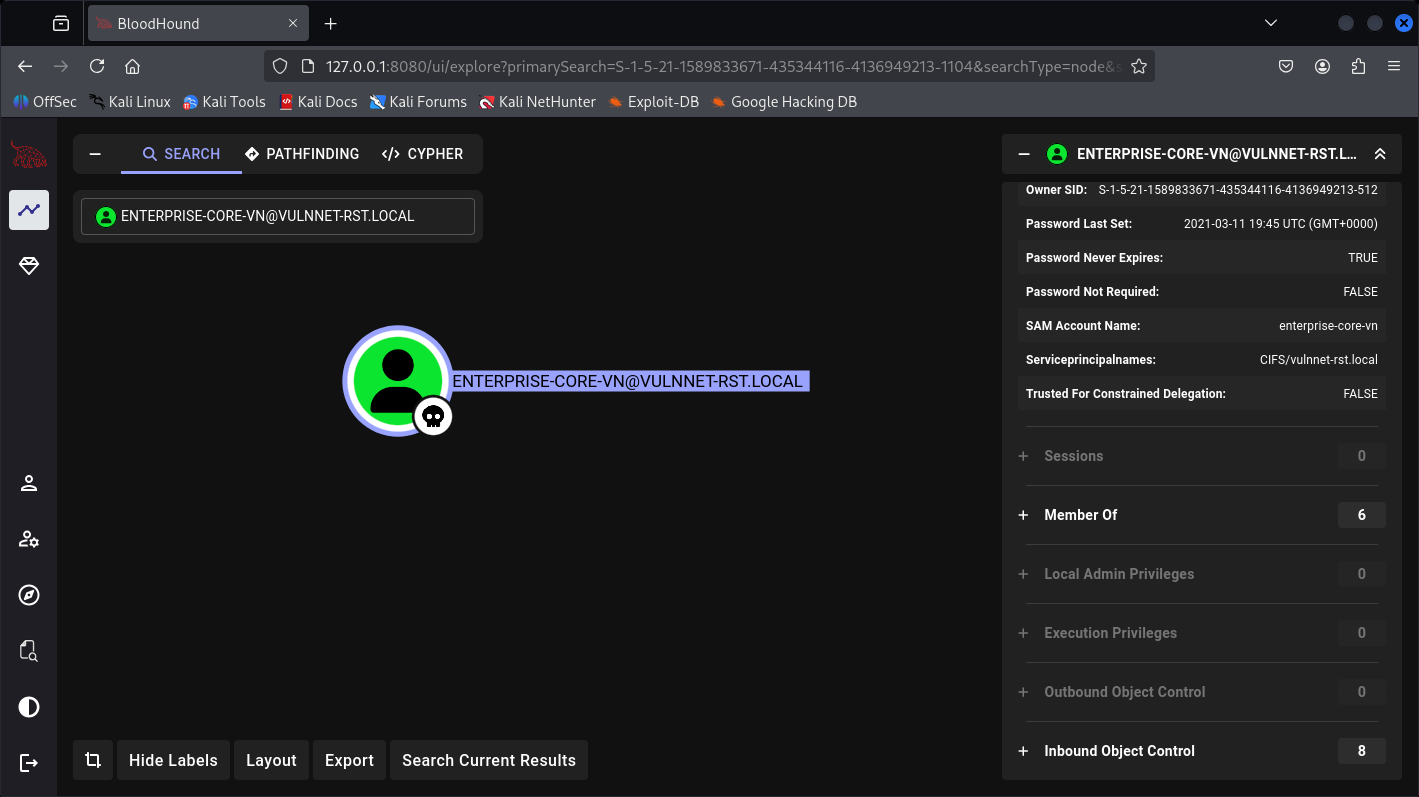
Kerberos Attack made Easy - AS-REP and TGS-REP
Collect Users from RID identification number to discover one of them leading to Kerberos pre-auth failing to AS-REP roast, then escalate wit

PEN-200 Practices - Active Directory Part 09
Craft Windows Username format via Web enumeration, elevate with AS-REP roasting to WinRM session login. PrivEsc with abusing group members o

PEN-200 Practices - Stand-alone (Windows) Part 08
Elevate your initial foot-hold around WebApp and SMB shares, gain machine initial access through reverse shell as User. PrivEsc with winPEAS

PEN-200 Practices - Active Directory Part 07
Active Directory (Full-case) Kerberos Based-attack for PEN-200 practices. Active Directory On this another internal PenTesting practices, th

PEN-200 Practices - Active Directory Part 06
Exploiting ADCS with category of ESC1 with escalation of CVE-2022-26923, adding a host for exploiting UPNs and SAN insecure unique DNS signa

PEN-200 Practices - Active Directory Part 05
Enumerating DC service ports and discover vulnerability through Windows version and NMAP Vuln script. Windows execution through Metasploit C